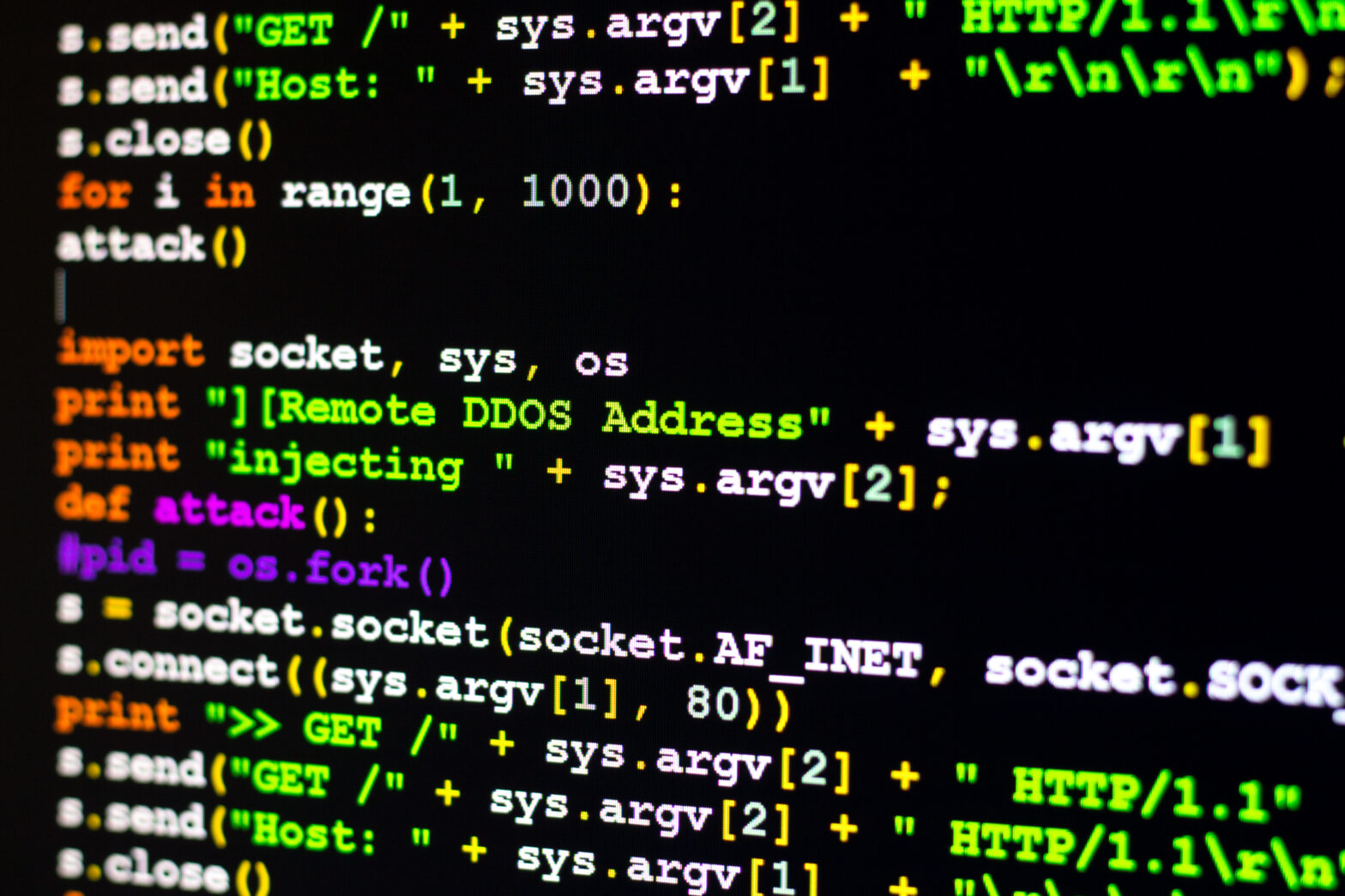
The source code used huge numbers of IoT connected devices to form a botnet, and attack websites with a DDoS attack, has been released by its author.
The malware, named ‘Mirai’, is a DDoS Trojan and targets Linux systems and, in particular, IoT devices.
Mirai finds smart devices – particularly in homes – that have weak passwords and takes control.
The source code is believed to have been leaked online in a hacking forum, and will most likely lead to an increase in large scale web attacks.
Mark James, security specialist at ESET said: “We will almost certainly see a surge in DDoS activity due to the release of this source code, if not for specific reasons than people having “a play” with the code to see what it does. The biggest problem is that by their very nature IoT devices are designed to be connected and often remotely managed.”
>See also: 5 cyber hacks that will affect your life in 2016
The Mirai DDoS Trojan was used to attack security blogger Brian Krebs’ website back on 20th September, where the attack pointed more than 620 gigabits of data every second at his site.
This attack, in terms of the amount of data being thrown at the website, was the biggest the web has ever seen. Although this was surpassed later that month in an attack on French hosting firm OVH which experienced a datastream of 1 terabit per second.
It has been suggested that the Mirai botnet and the programme used to attack OVH have control of an estimated 1.2 million vulnerable devices.
The problem is that the passwords used to manage these smart devices are not strong enough, or encrypted properly.
Jon Geater, CTO at Thales e-Security confirms that “the prevalence and relative simplicity of DDOS attacks show that it is still necessary to practice security by design, such as encryption and signing techniques, and not simply rely on online systems and ‘big data’ for your security.”
>See also: Top 5 mobile app monetisation hacks
The reason so many IoT devices use default passwords, suggests Stephen Gates, chief research intelligence analyst at NSFOCUS is that when “manufacturers build this type of technology they make it as “user-friendly” as possible.
“The real intention of the decision to ship every device with the same username/password is primarily designed to reduce customer support calls; which costs manufacturers money.”
Indeed, the security of these devices needs to be improved drastically in light of the release of this malicious computer code, because societies are entering a phase where more and more devices are connected.
Protecting this increased connectivity is vital.
A data-centric security approach that helps prevent data leakage and access is a valid security option according to Reiner Kappenberger, global product manager at HPE Security – Data Security.
“Innovative technologies such as industry-standard format-preserving encryption can protect data, at the data level, in the IoT mobile applications, in connected devices and in the enterprise back-end systems.”