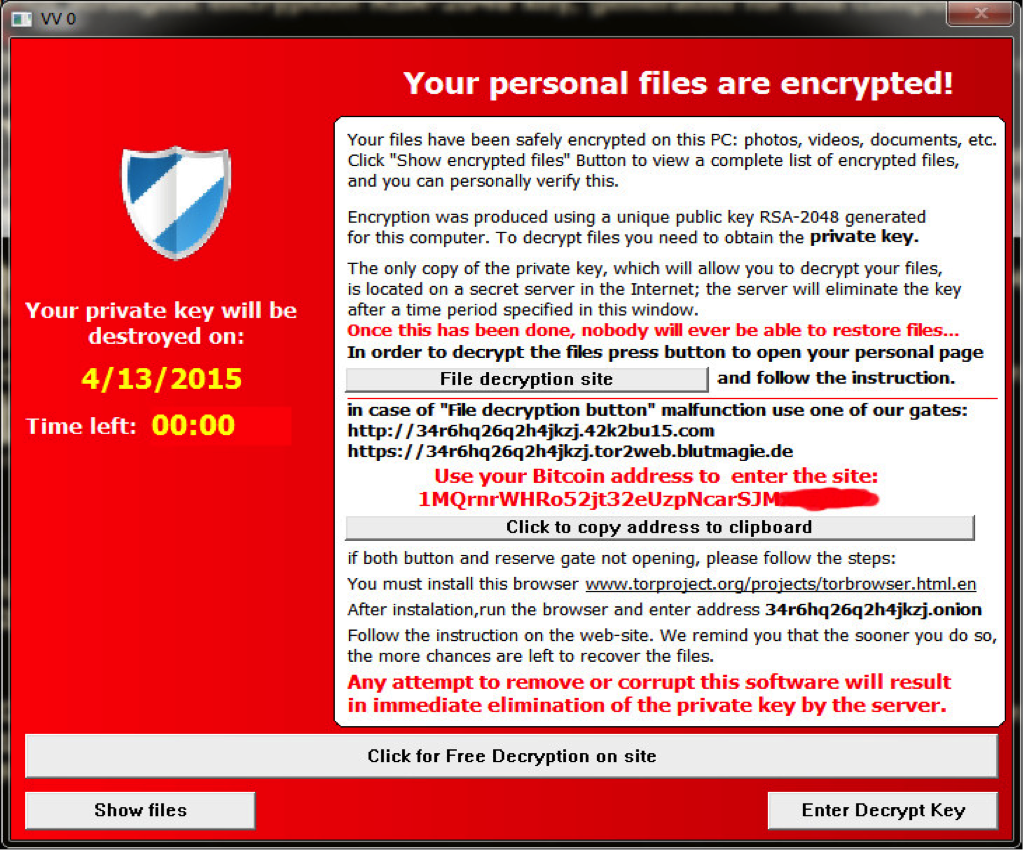
The recent spate of ransomware attacks, has sparked fresh concerns for European and US organisations as attacks have become more widespread and damaging. Ransomware is the name of a type of malware that encrypts a computer and/or its files, rendering it unusable to the victims until they pay the attacker’s requested ransom to get the decryption key.
The latest variants use stealthy techniques to dupe unwitting victims – from phishing campaigns to malvertising campaigns in which malicious ads can be found on legitimate websites. If users click on the ads, they can be redirected to sites hosting exploit kits that check their machines for out-of-date software to exploit.
Whilst many attacks are opportunistic in nature, there are now signs of more targeted attacks focussed on high profile targets for maximum ransom return, often ranging from £100 to £1000 worth of bitcoins. So how can organisations best protect their networks against this new, and more troubling, breed of ransomware?
The ransomware crime wave
The recent ransomware crime wave has left a trail of victims, forcing organisations to re-examine their security policies. One variant of ransomware to have hit the headlines is Petya.
> See also: How to make your data immune to ransomware
This is a particularly nasty form of attack that works by encrypting an entire hard drive. It has been spread by unsuspecting users simply clicking on a link in an innocent looking email.
There have also been reports that TeslaCrypt 2.0, a file-encrypting ransomware has spread across Europe through a new spam campaign, affecting countries including Germany, UK, France, Italy and Spain. After locking users out of their system, attackers will demand a ransom.
In the US, the health sector has recently been hit by a growing ransomware threat, with attackers intent on extorting money from hospitals by infecting, locking and shutting down systems.
These have not only caused massive disruption to systems but have also impacted patient care, when treatment records, such as CT scans and X-rays could not be easily shared.
In one attack, in which a Kentucky hospital was struck by a variant of ransomware known as Locky, patients’ files were copied and locked, and attackers demanded four bitcoins ($1600) to unlock the encrypted backups.
What was particularly significant about this latest strain was that it tried to spread itself to the entire internal network. In a separate attack, the Hollywood Presbyterian Hospital in Los Angeles was reported to have paid a ransom of $17,000 to regain access to its systems.
Get the basics right
Generally, attackers strike by exploiting known vulnerabilities in outdated systems. One example is Silverlight CVE-2016-0034 which installs TeslaCrypt on user systems. This critical vulnerability was patched by Microsoft in January, but any systems that aren’t fully patched to the latest version may still be vulnerable.
> See also: How to prevent ransomware running off with your cash
Whilst attackers are looking for vulnerabilities to exploit, organisations can take steps to reduce their risk of infection and this comes down to basic security best practices:
- Make sure all software is up to date – attackers will exploit out-of-date systems so ensure you have the latest versions on every browser and operating systems Flash, Java, etc.
- Prioritise patching for Flash and Silverlight vulnerabilities.
- Uninstall rarely-used software. If there’s not a business need for certain plugins, then disable them, or enable click-to-play.
- Keep important files backed up, and make sure these back-ups are on media that is physically disconnected from your local system – such as the cloud or an external drive. Don’t keep important data on the local drive.
- It’s important to keep backups disconnected, as TeslaCrypt and other types of ransomware will encrypt any connected drives/network folders and the local drive.
- Exercise caution with links and attachments. Don’t open anything from untrusted sources – don’t download or open .zip attachments in spam email. Keep your IT or security team informed of suspicious activity to help contain the spread of malware.
- Enable two-factor authentication on all of your logins to protect against an attack that leverages stolen passwords to access your accounts.
Whilst we can’t stop cyber criminals from developing new, and stealthier means of attack, these straightforward measures can help to minimise the risk of falling victim to this modern crime wave.
Sourced from Mike Hanley, Director of Duo Labs, Duo Security