Avast’s threat labs researchers have intercepted and protected users against a rise in phishing sites focused on cryptocurrency scams since the start of the year, with the majority posing as legitimate custodial wallets.
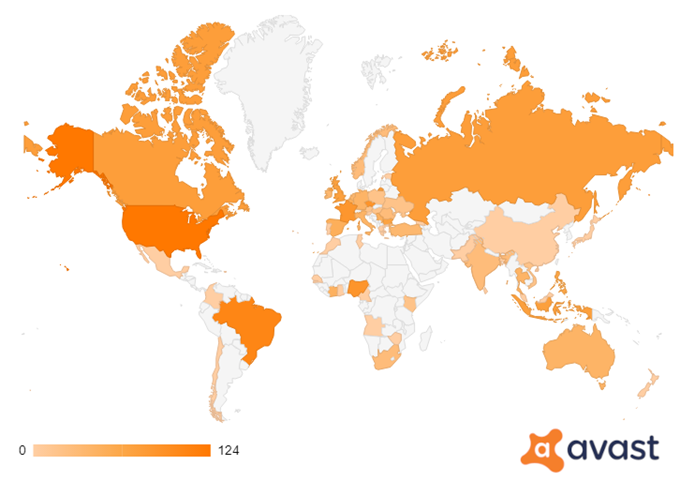
The US, Brazil and Nigeria were found to be the biggest targets for these crypto scams, with notable levels of scams also in the UK, France, Russia and India, following the monitoring of a selection of 37 samples.
“The crypto market is surging right now. Bitcoin has been given a boost, following recent news from El Salvador that it will be recognised as legal tender in the country – with other countries in the region tipped to follow suit,” said Peter Kovac, senior researcher at Avast.
“This surge in Bitcoin is having a knock-on effect across the wider crypto space, and some analysts are even predicting that 2021 will be a record-breaking year for cryptocurrencies.
“However, as it has grown in popularity, it has also grown as a more lucrative target for hackers – and our researchers have found the levels of crypto-related scams are most prevalent in regions where cryptocurrencies are gaining popularity.”
Keeping cryptocurrency safe
Cryptocurrency scams can come in many forms online, so to protect from such risks, Avast recommends the following tips:
- Watch out for unsolicited private messages: Users should look to immediately block any unsolicited message on social media that may be fraud, such as an unknown number.
- Be aware of mobile phishing: Hackers are increasingly targeting people on their mobile devices in order to steal crypto credentials, with attacks coming from texts, social media, third-party messaging platforms or email, among other methods. To prevent mobile phishing attacks, users can use a secure browser that offers an anti-phishing feature for blocking malicious sites on Android devices.
- Rely on services that use strong security measures: When choosing a custodial or software wallet, users should choose a provider that offers strong security measures, including multi-factor authentication.
- Install an antivirus: Crypto owners should ensure that they have strong antivirus protection across all devices. Malicious mobile phishing and malware campaigns have frequently found success due to a lack of this kind of protection.
How cryptocurrency wallets can be safeguarded through biometrics
Ways to store cryptocurrency
Avast has provided advice on how to store cryptocurrencies, citing the following methods, along with their pros and cons:
- Custodian wallets: Frequently imitated by sites set up by scammers, custodian wallets operate like a traditional bank account, where users can log in and manage their funds. The burden of securing funds is partially offloaded to the service provider, with users gaining guarantees and insurance to a certain extent. However, funds may be lost if the service is bankrupt or fraudulent, which could lead to the service provider limiting access to funds.
- Software wallets: Software wallets are applications that manage cryptocurrency owners’ private keys and allow them to make transactions directly. While they tend to allow for more user control than custodian wallets, the device the software wallet is stored on will be the single point of failure, meaning that if hacked, the user could lose access permanently.
- Hardware wallets: Hardware wallets come in the form of a separate device, such as a USB. While these are especially designed to prevent hacking, with only very select, skilled individuals demonstrating the ability to infiltrate them, there is always the risk of losing the device, and in turn the user’s funds.
- Paper and brain wallets: There is also the option of having the private key written down or memorised. While simpler and lower cost by comparison, there is the risk of losing funds if the paper is damaged or stolen, or there is a lapse in memory.







