Every day hundreds of network security devices generate millions of log files, creating a detailed millisecond-by-millisecond record of all authorised and unauthorised user activity. Finding a way to extract meaningful evidence of cyber threat activity from this vast data set is crucial to the long-term security of any organisation.
In the past few years the risk of becoming the next victim of a cyber attack has increased exponentially despite the seemingly endless array of new technologies designed to thwart the would-be hackers. Today it is more a question of “when” rather than “if” your network will be breached and the chances are that this may have already happened but it just hasn’t manifested itself yet.
There is little doubt that hacking is now becoming a career choice for many individuals, with excellent prospects for future earnings potential. Like many legitimate industries, hacking is continually evolving its approach and techniques to keep ahead of the competition, the “white hats”, to maintain and grow its revenue streams.
This means businesses have no choice but to up their game and develop smarter ways to try to get at least one step ahead in the battle to defend their networks, rather than playing catch-up following the latest zero-day attack.
>See also: Top 10 predictions for low-level cybercrime in 2017
Security log files have long been recognised as one way of monitoring internal and external suspect activity. There is now a wide range of IDS/IPS and SIEM solutions available that are designed to alert CISOs when a particular red flag is triggered, maybe indicating an attack is in progress or someone is attempting to access a restricted area of the network.
Clearly a useful tool and with unlimited time and resources a CISO may be able to extrapolate more granular information from their SIEM reports that can help in developing effective remediation strategies. However, the reality is that few have the spare capacity needed to divert away from their routine maintenance and firefighting tasks to devote time to the strategic analysis of the data.
Fortunately, a new generation of data analytics tools is now emerging that are capable of doing the heavy lifting in terms of processing the millions of logs from across the network at gigabyte-per-second speeds. Using advanced pattern matching and machine learning techniques, CISOs can now obtain a detailed forensic understanding of where any previously undetected vulnerabilities are in the system, evidence of data exfiltration, attack sources and targets, and incidences of compromise, matched against thousands of known and zero-day threats.
This represents a step-change in cyber-protection techniques available to those responsible for network security that can not only benchmark the current network security status but can also help to identify previously undetected attacks and evidence of future threat vectors that may have laid dormant for several months.
Typically, these tools include a graphical management dashboard incorporating a range of charts and diagrams that provide a visual representation and breakdown of the critical attack parameters, rather than requiring the user to spend hours trawling through hundreds of columns of spreadsheet data to identify the tell-tale signs of hacker activity.
While most IT pros are likely to be familiar with this type of GU interface and can quickly assess the general implications the information represents from the visual clues, turning this into actionable intelligence can still require additional time and a degree of specialist analysis of individual data points to enable informed decision making.
Many businesses and organisations are increasingly using advanced customer and market data analytics to support their business decision making and can maybe afford to employ specialist data analysts spending weeks or months producing their management reports. However in the world of cyber security, even a few hours delay in acting on threat intelligence could make the difference between preventing or succumbing to a financially or operationally damaging attack.
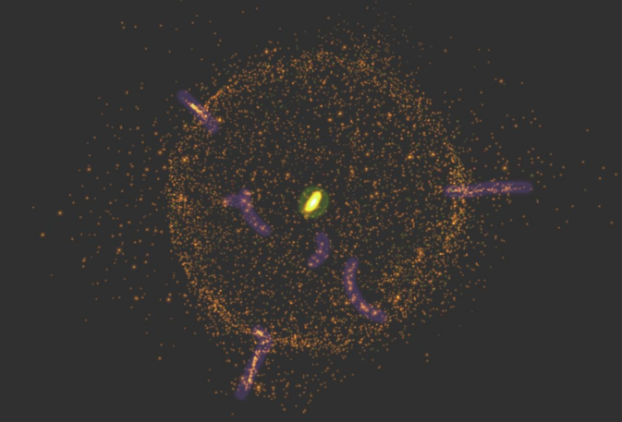
What is needed is a new way of visualising data that utilises our most advanced human sense to the maximum effectiveness. According to one leading data journalist and information designer, David McCandless, sight has by far the fastest and biggest bandwidth of any of the five senses with about 80% of the information we take in being through the eye.
The very latest data visualisation interface that is emerging has been developed to exploit this natural ability to process information that most of us have, to create an augmented intelligence platform. This projects the scanned data using custom algorithms aimed at highlighting patterns in a dynamic 3D ‘threat universe’ format, providing security analysts with a highly granular, visual image of the data.
>See also: The role of AI in cyber security
Representing a new-wave of threat intelligence based forensic techniques, CISOs are able to take a 30,000ft view of the entire data cloud and see the trends and patterns in the attack ecosystem, at scale, that would otherwise could take weeks or months to detect using the traditional, non-visual methodologies and tools.
By visualising the complete threat space for their organisation, security analysts are able to rapidly assess the historic and current threat profile of their entire network infrastructure to predict and prevent future attacks.
In the increasingly hostile world of cyber security where even major public sector institutions can be brought to a halt through a malware attack, organisations need to stay vigilant and use all the tools at their disposal to proactively seek and block threats before they can become active. These new high-speed data analytics and advanced visualisation platforms could be the answer in the ongoing arms race with the global hacker industry.
Sourced from Richard Benson, CEO, Xanadata